Prerequisite
Install the dedicated package on the server:
| Tabs group |
|---|
| border | all-sides |
|---|
| navcolor | navy |
|---|
|
| Ubuntu/Debian aptitude install bm-plugin-hps-kerberos RedHat/CentOSyum install bm-plugin-hps-kerberos |
- Create a service user for Kerberos authentication in the Active Directory, e.g. bmkrb with the password "krbpwd".
Open a "cmd.exe" console and run the following command:
| Bloc de code |
|---|
setspn -A HTTP/bluemind.domain.tld bmkrb |
This command should return a result similar to the following lines:
| Bloc de code |
|---|
Registering ServicePrincipalNames for CN=bmkrb,CN=Users,DC=domain,DC=tld
HTTP/bluemind.domain.tld
Updated object |
Run the following command:
| Bloc de code |
|---|
ktpass /out C:\hps.keytab /mapuser bmkrb@DOMAIN.TLD /princ HTTP/bluemind.domain.tld@DOMAIN.TLD /pass krbpwd /kvno 0 /ptype KRB5_NT_PRINCIPAL |
The result should look like this:
| Bloc de code |
|---|
Targeting domain controller: AD.domain.tld
Using legacy password setting method
Successfully mapped HTTP/bluemind.domain.tld to bmkrb.
Output keytab to C:\hps.keytab |
Setting up Kerberos in the admin console
- As admin0 go to System Management -> System Configuration -> Authentication tab.
- Select Kerberos as authentication mode from the drop-down menu and fill in the related authentication settings (the keytab file requested is: C:\hps.keytab previously exported on the Kerberos server)
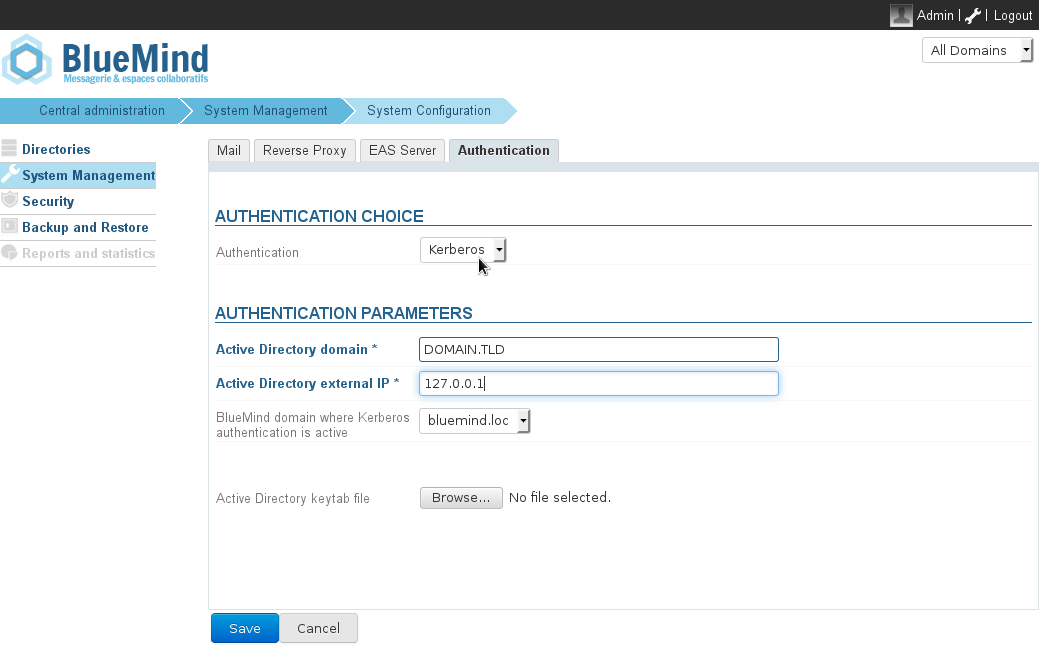
- Save. You will be required to restart the bm-hps service.
| Info |
|---|
Once Kerberos authentication is enabled, you will be automatically authenticated if your browser is configured correctly. If you want to connect as admin0 or on another domain, go to the page: bm.domain.tld/native. |
Setting up Kerberos manually
This section describes how to configure Kerberos authentication manually. However, you might also find this paragraph useful if your Kerberos domain name is different from your BlueMind domain name.
- Copy the file "C:\hps.keytab" from the Kerberos server to the BlueMind server into "/etc/bm-hps/"
- Copy the file "
/etc/bm/default/bm-hps.ini" to "/etc/bm/local/bm-hps.ini" - Go to the web page httphttps://gitgithub.bluecom/bluemind-mind.net/bluemind/tree/release/3/conf/bm-hps/kerberos/hps-kerberos-sample to download the sample files mem_confbm-hps.ini, jaas.conf and krb5.ini
- Copy the files "jaas.con"f and "krb5.ini" in the "
/etc/bm-hps" directory of the BlueMind server Copy the contents of the file "mem_confbm-hps.ini" into the file copied previously "/etc/bm/local/bm-hps.ini"
- In "jaas.conf", change the following information:
- principal="HTTP/bluemind.domain.tld@DOMAIN.TLD"
- In krb5.ini, change the following information:
- default_realm = DOMAIN.TLD
- In [ realms ], DOMAIN.TLD = { kdc = <ip_ad_server>:88 }
- In [ domain_realm ], domain.tld = DOMAIN.TLD and .domain.tld = DOMAIN.TLD
| Avertissement |
|---|
|
The Active Directory domain name must be written in CAPITAL LETTERS in the configuration file, failing that it will not work. |
Setting up different domains for Kerberos and BlueMind
Since BlueMind v.3.0.7, you can set up authentication with different domains for Kerberos and BlueMind.
Server configuration
Create a new configuration file /etc/bm-hps/mappings.ini with the following contents:
| Bloc de code |
|---|
[bm_mappings]
DOMAINEAD.LAN=domaineBM.vmw |
In this instance, DOMAINEAD.LAN is your AD domain and domaineBM.vmw is your BlueMind domain.
When the file has been created, restart BlueMind:
| Bloc de code |
|---|
bmctl restart |
Client configuration
When the AD domain is different from the BlueMind domain, the client web browser may not trust the BlueMind domain. The BlueMind url access must therefore be added as a trusted site in the web browser.
Firefox
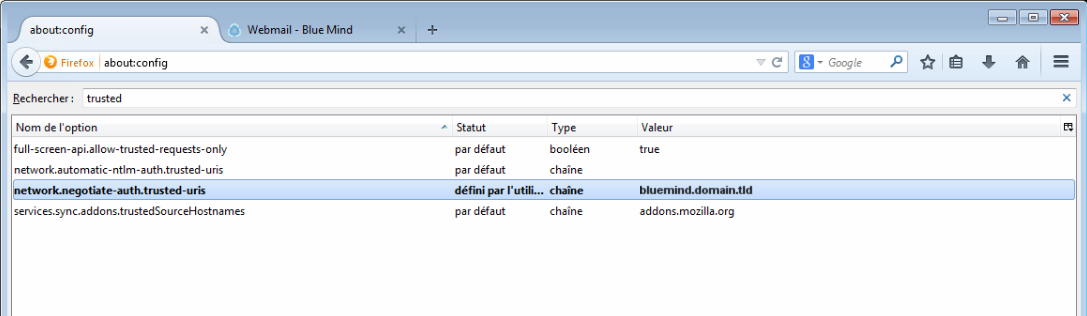
To add a trusted site, you need to access the Firefox configuration settings. To do this:
Internet Explorer
Trusted sites are configured in the Internet Options window:
- Go to the Tools menu > Internet Options
- In the Security tab, select Local Intranet and click "Sites"
- In the dialog box that opens, click "Advanced"
- Fill in the "Add this website to the zone" box and click "Add". The site should be added to the list of websites underneath.
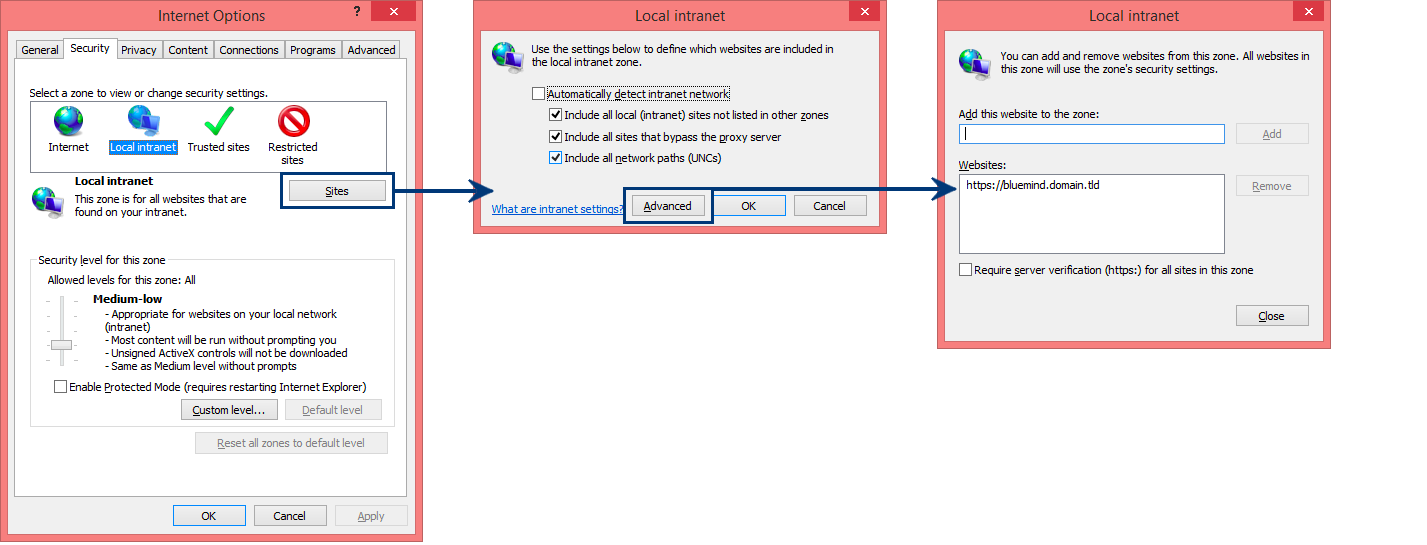
- Click "Close" to quit, then "OK" in the second dialog box, and finally "OK" in the first one.
- Restart the web browser to apply the change.
Chrome
Chrome is based on the Internet Explorer configuration. As a result, in Windows, simply follow the same process as above to add a new site to the trusted list.
For other operating systems, however, use the following command line to add a trusted website:
| Bloc de code |
|---|
google-chrome --auth-server-whitelist="*bluemind.domain.tld"
|
References
For more information, please look at the following pages:
http://sammoffatt.com.au/jauthtools/Kerberos/Browser_Support
http://support.microsoft.com/kb/303650